Question 1 - Run a sub-domain/vhost fuzzing scan on ‘*.academy.htb’ for the IP shown above. What are all the sub-domains you can identify? (Only write the sub-domain name)
- Well this is straight forward, let’s use
subdomains-top1million-5000. - Don’t forget to add ip in your
hostsfile.ffuf -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://academy.htb:<port>/ -H 'Host: FUZZ.academy.htb'

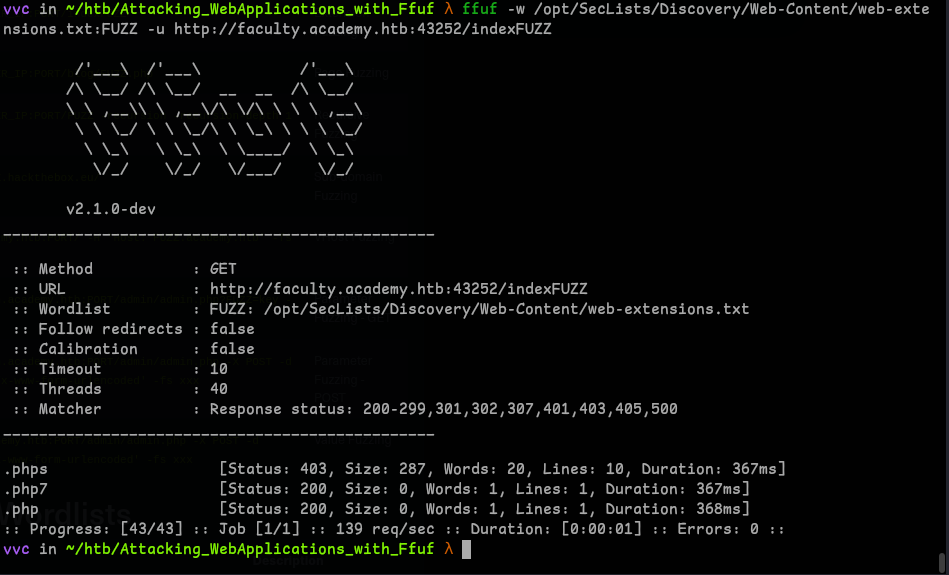
Question 2 - Before you run your page fuzzing scan, you should first run an extension fuzzing scan. What are the different extensions accepted by the domains?
- Okay, Let’s use web-extensions.txt wordlist, pretty straight-forward.
- I tried fuzzing on 3 different vhosts that we found, and we got our answer.
ffuf -w /opt/SecLists/Discovery/Web-Content/web-extensions.txt:FUZZ -u http://faculty.academy.htb:43252/indexFUZZ
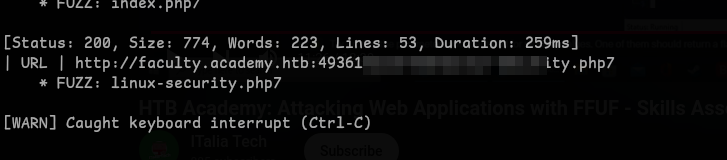
Question 3 - One of the pages you will identify should say ‘You don’t have access!’. What is the full page URL?
-
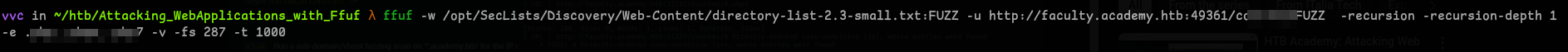
We have to fuzz on all of our vhosts with recursion and the extensions that we just found.
-
I just checked the hint :)
-
Also with 1000 threads.. :?
ffuf -w /opt/SecLists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt:FUZZ -u http://vhost.academy.htb:PORT/FUZZ -recursion -recursion-depth 1 -e .ext1,.ext2,.ext3 -v -fs <xxx> -t 1000
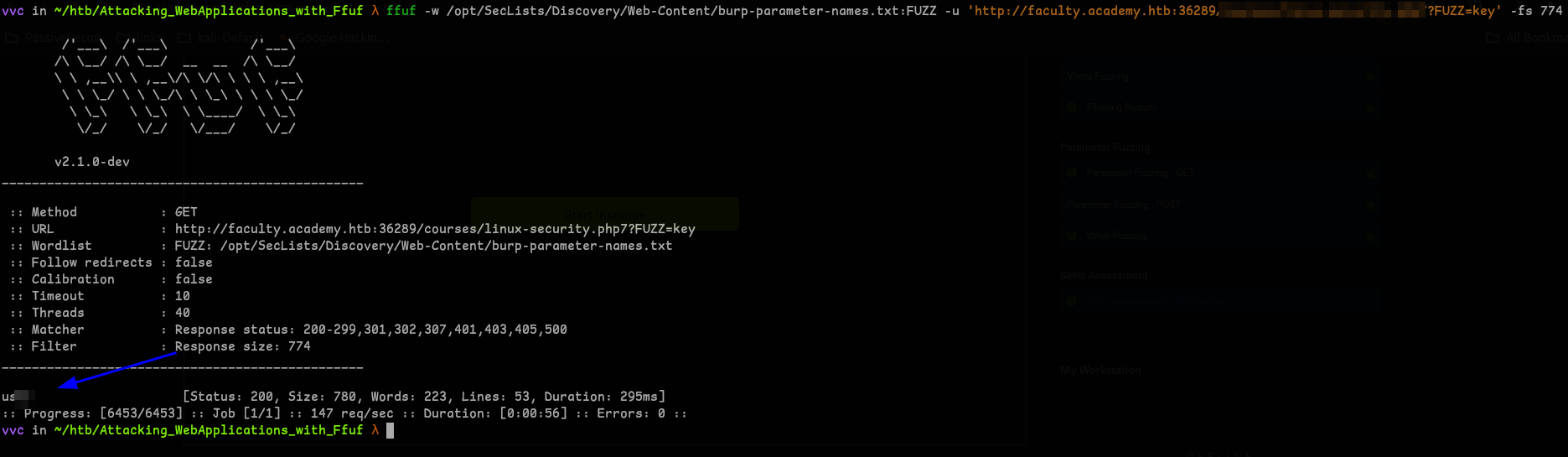
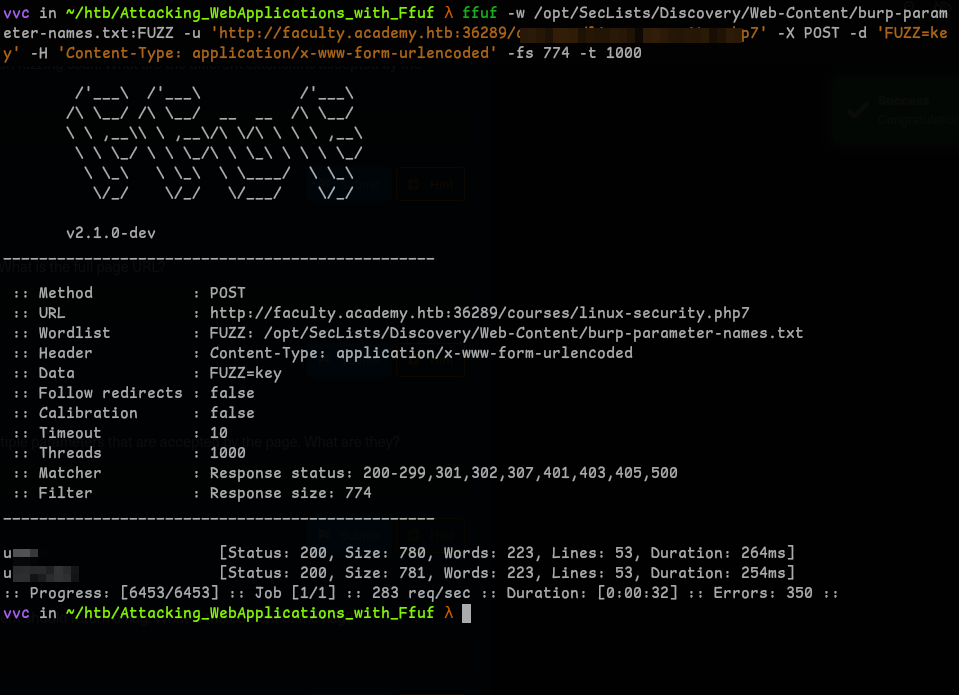
Question 4 - In the page from the previous question, you should be able to find multiple parameters that are accepted by the page. What are they?
-
Well, we should find the parameters first.. so..
burp-parameter-names.txt -
I got the answer, and gave it as answer.. it’s wrong.. because I didn’t read the question properly.. question is expecting more parameters..
-
so:
ffuf -w /opt/SecLists/Discovery/Web-Content/burp-parameter-names.txt:FUZZ -u '<url>' -X POST -d 'FUZZ=key' -H 'Content-Type: application/x-www-form-urlencoded' -fs xxx
Question 5 - Try fuzzing the parameters you identified for working values. One of them should return a flag. What is the content of the flag?
-
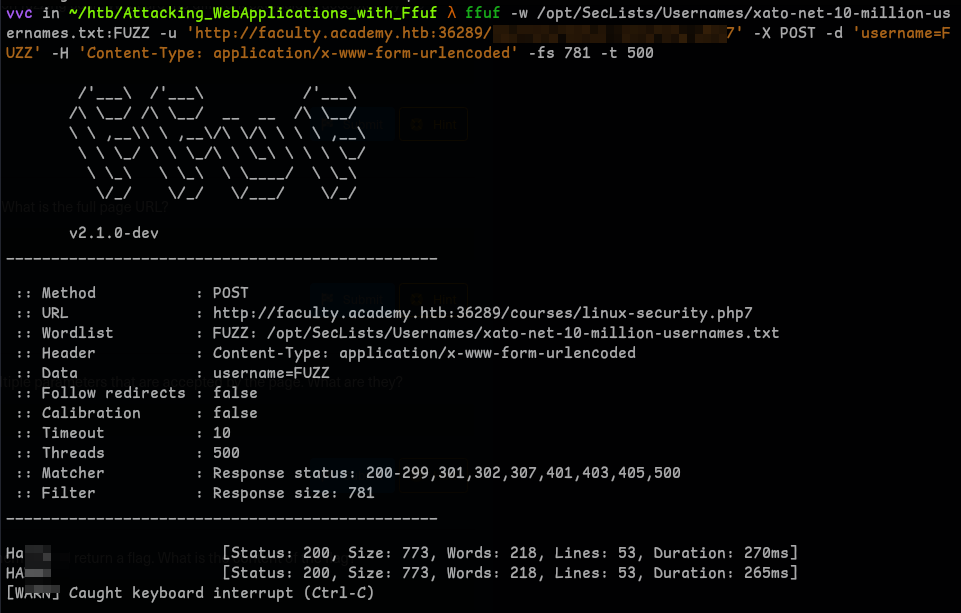
First we have to find valid usernames..
-
I tried different wordlists and finally got the answer with
xato-net-10-million-usernames.txtwordlist.ffuf -w /opt/SecLists/Usernames/xato-net-10-million-usernames.txt:FUZZ -u '<url>' -X POST -d 'username=FUZZ' -H 'Content-Type: application/x-www-form-urlencoded' -fs 781 -t 500
-
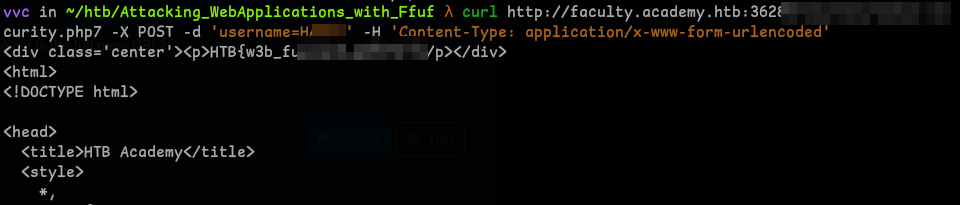
Now, that we have our usernames.. let’s just curl it!!
curl <url> -X POST -d 'username=<user>' -H 'Content-Type: application/x-www-form-urlencoded' -
Andd we got the flag :)